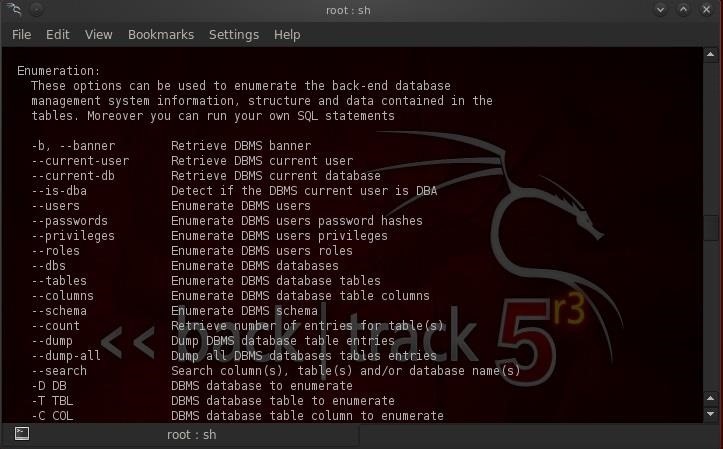
How to Hack Databases: Extracting Data from Online Databases Using Sqlmap « Null Byte :: WonderHowTo
3D Hacking Code Data Flow Stream on Green. Screen with Typing Coding Symbols Editorial Stock Photo - Image of language, blockchain: 150730668
3D Hacking Code Data Flow Stream on Black. Screen with Typing Coding Symbols Editorial Stock Photo - Image of crime, hack: 150731378














![98 Biggest Data Breaches, Hacks, and Exposures [2022 Update] - Termly 98 Biggest Data Breaches, Hacks, and Exposures [2022 Update] - Termly](https://termly.io/wp-content/uploads/Biggest_Data_Breaches_Ever.jpeg)






