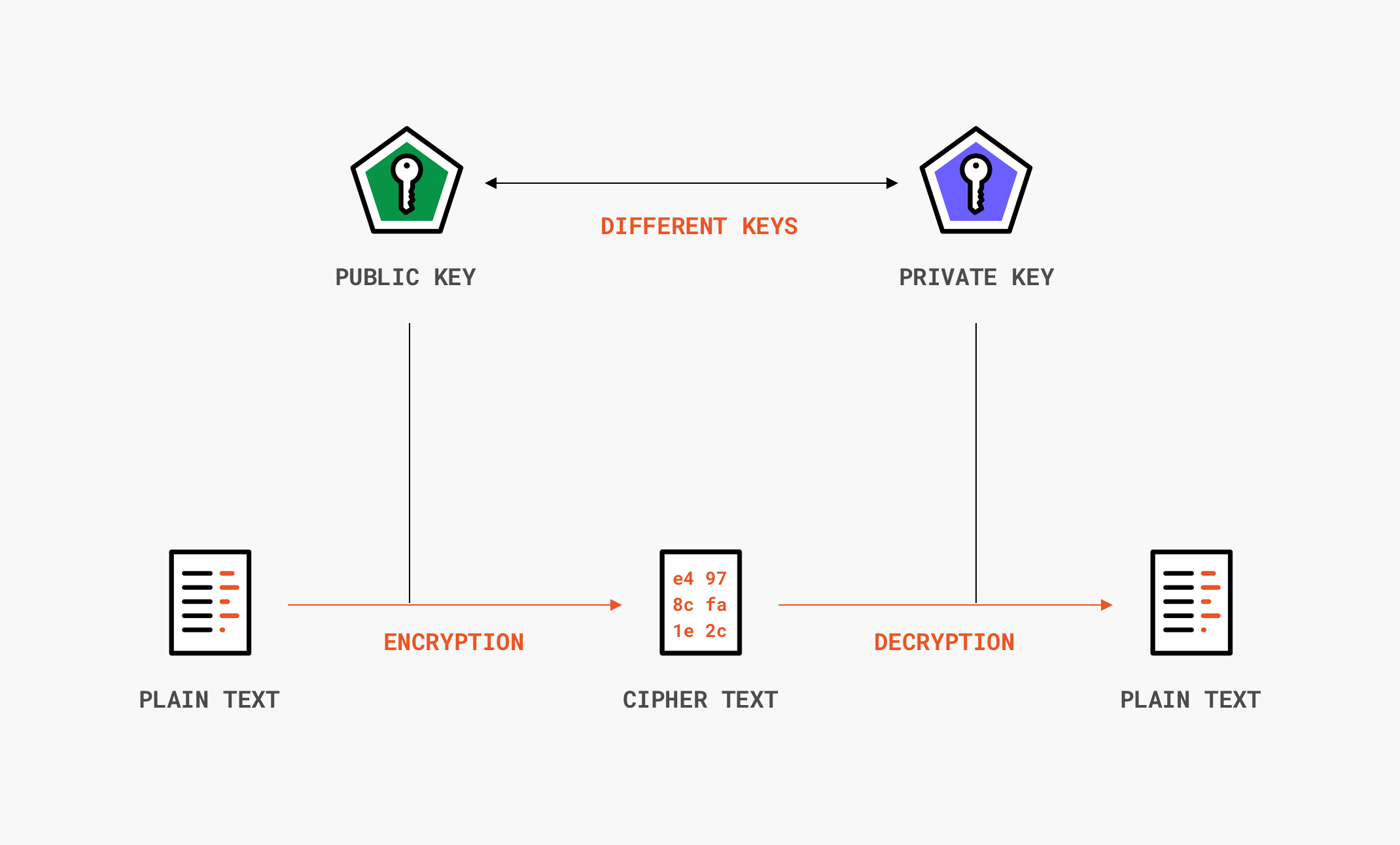
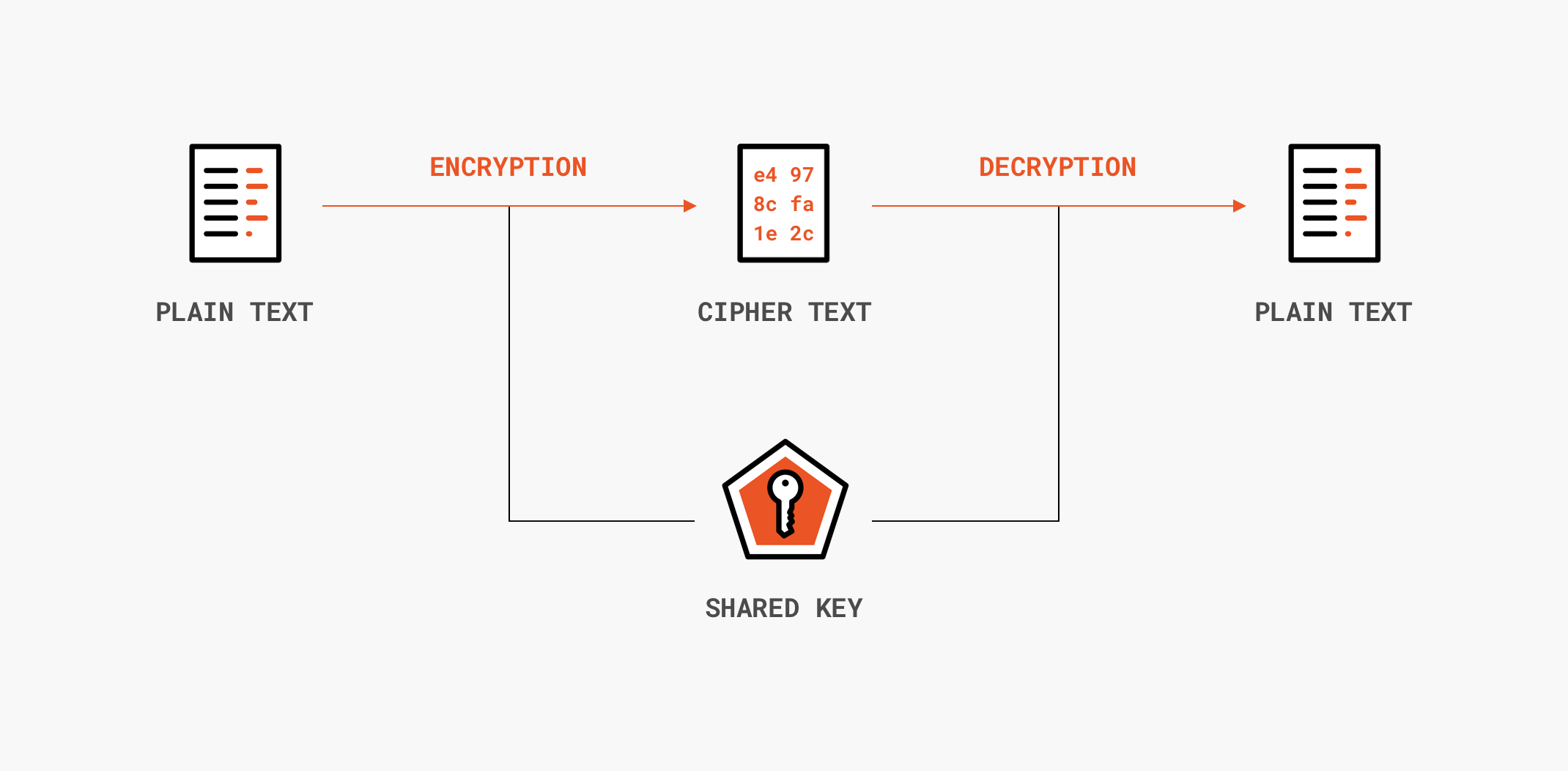
WHAT THE HASH? Data Integrity and Authenticity in American Jurisprudence - United States Cybersecurity Magazine

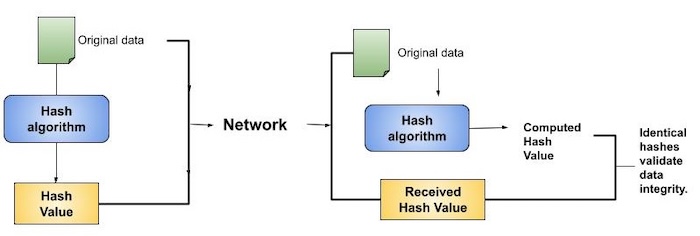
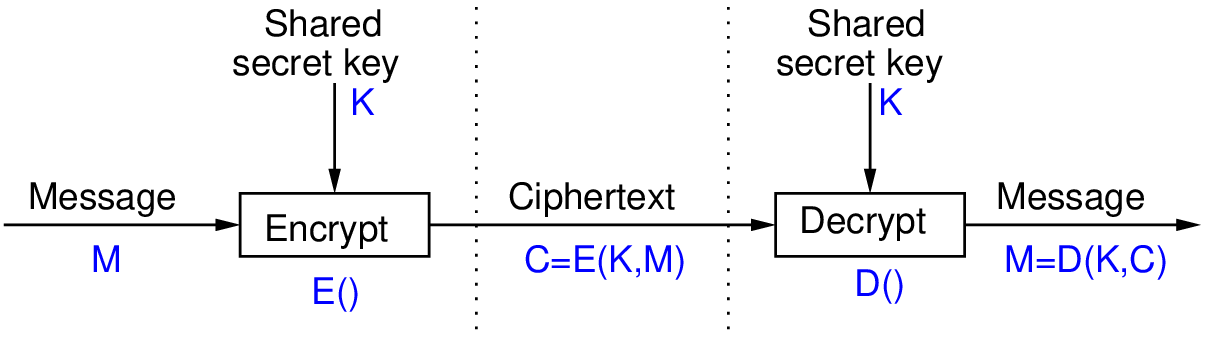
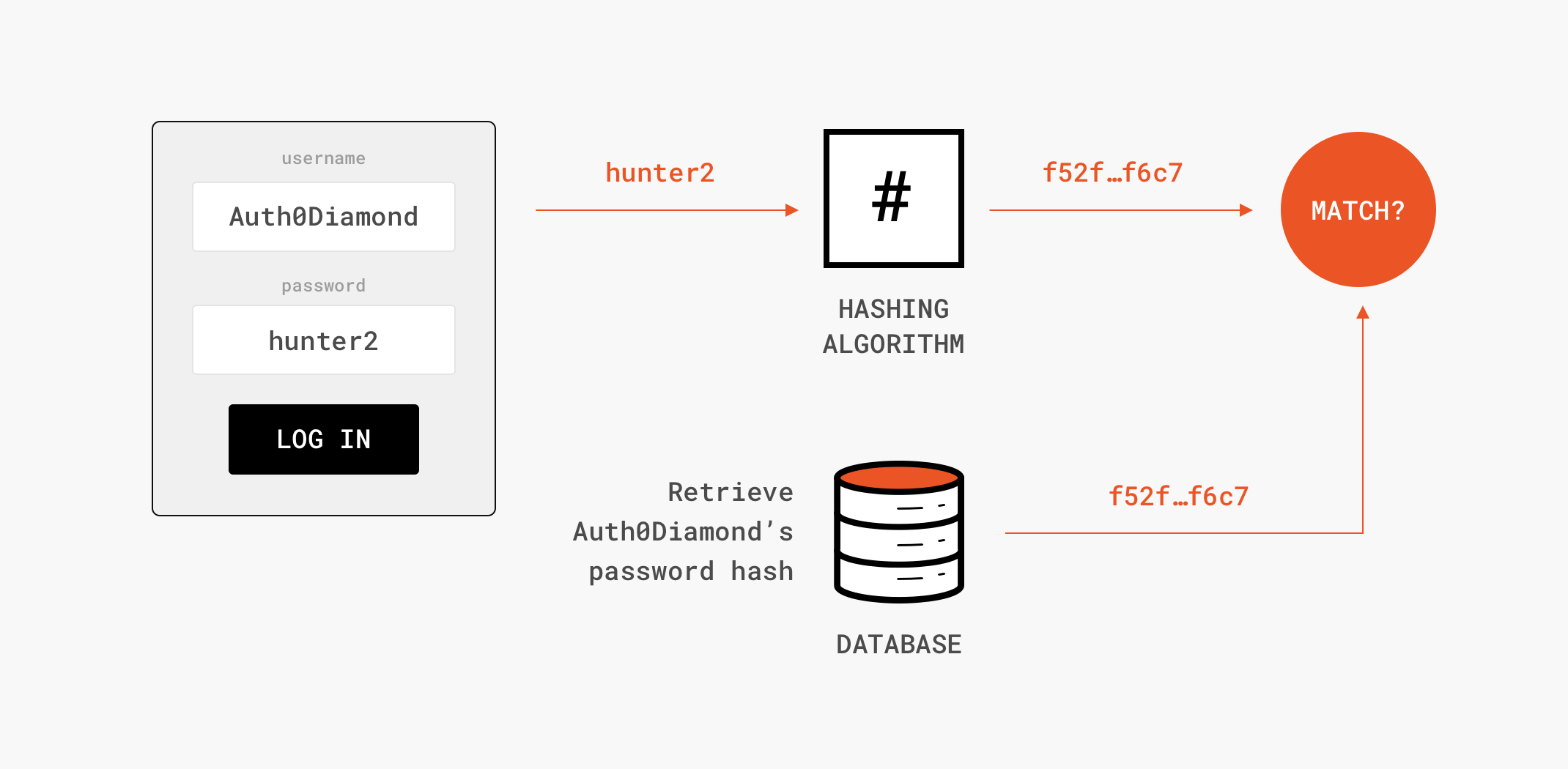
Ensuring integrity, authenticity, and non-repudiation in data transmission using node.js | by Glauber | GeeKoffee | Medium

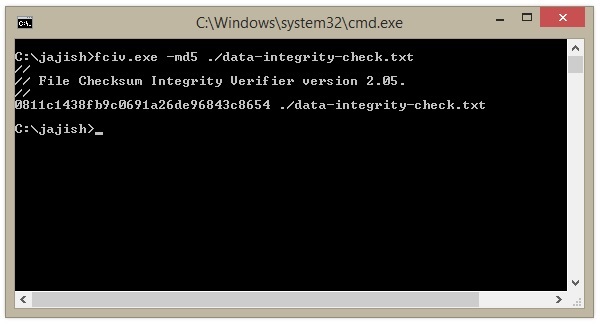
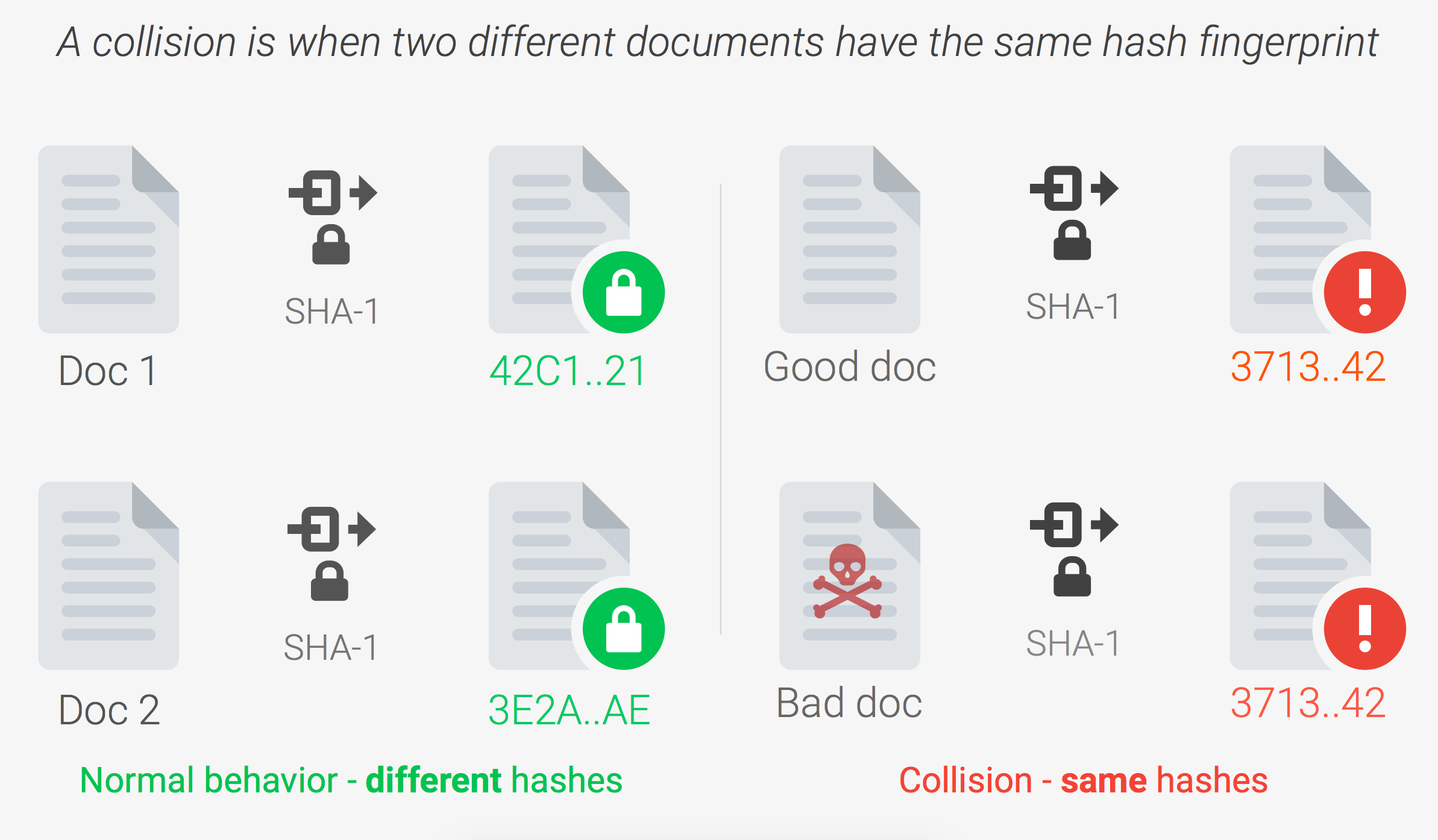
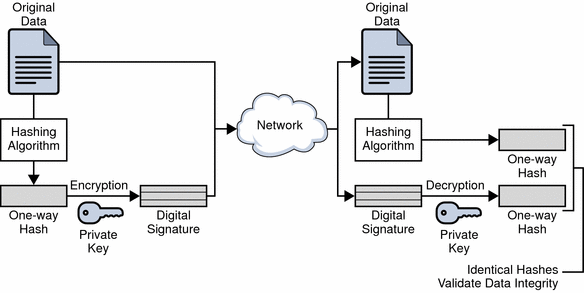
Using a Digital Signature to Validate Data Integrity Figure 2 shows two... | Download Scientific Diagram


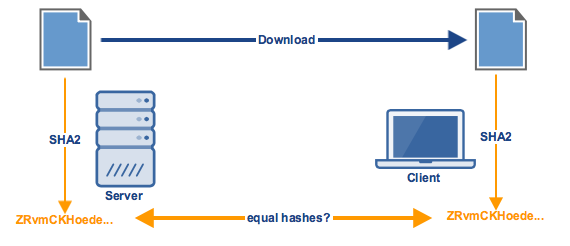
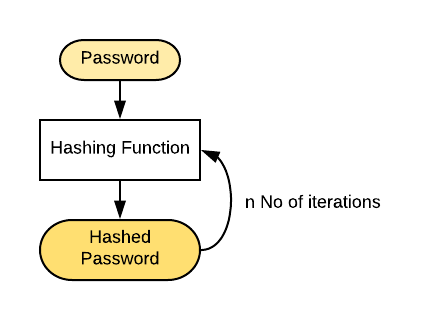
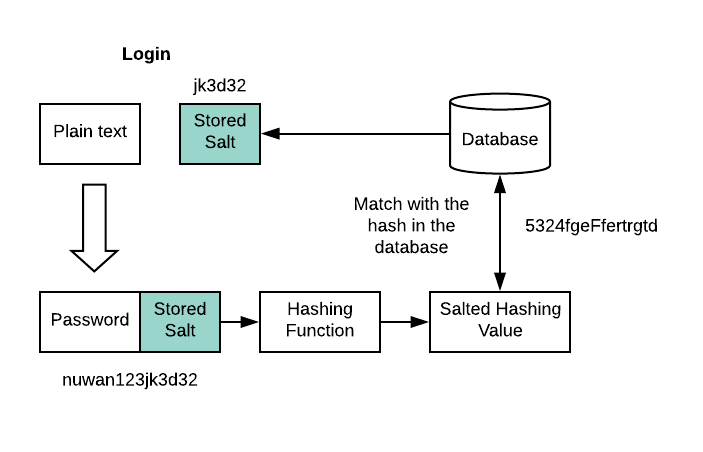
![What Is a Hash Function Within Cryptography [Quick Guide] - Security Boulevard What Is a Hash Function Within Cryptography [Quick Guide] - Security Boulevard](https://positiwise.com/wp-content/uploads/2022/06/hash-function.png)